This guide explains how to configure Microsoft Entra ID (formerly known as Azure Active Directory or Azure AD) with Redocly SSO and role-based access controls.
You need to complete all steps before you can test that the integration is working.
Start configuring SSO in Redocly to get the values needed for the next steps.
- Go to the Redocly Reunite dashboard and select SSO and login in the navigation.
- Select Add in the Guest or Corporate Identity Provider section.
- Select SAML2.
The following screenshot shows the SSO configuration screen.
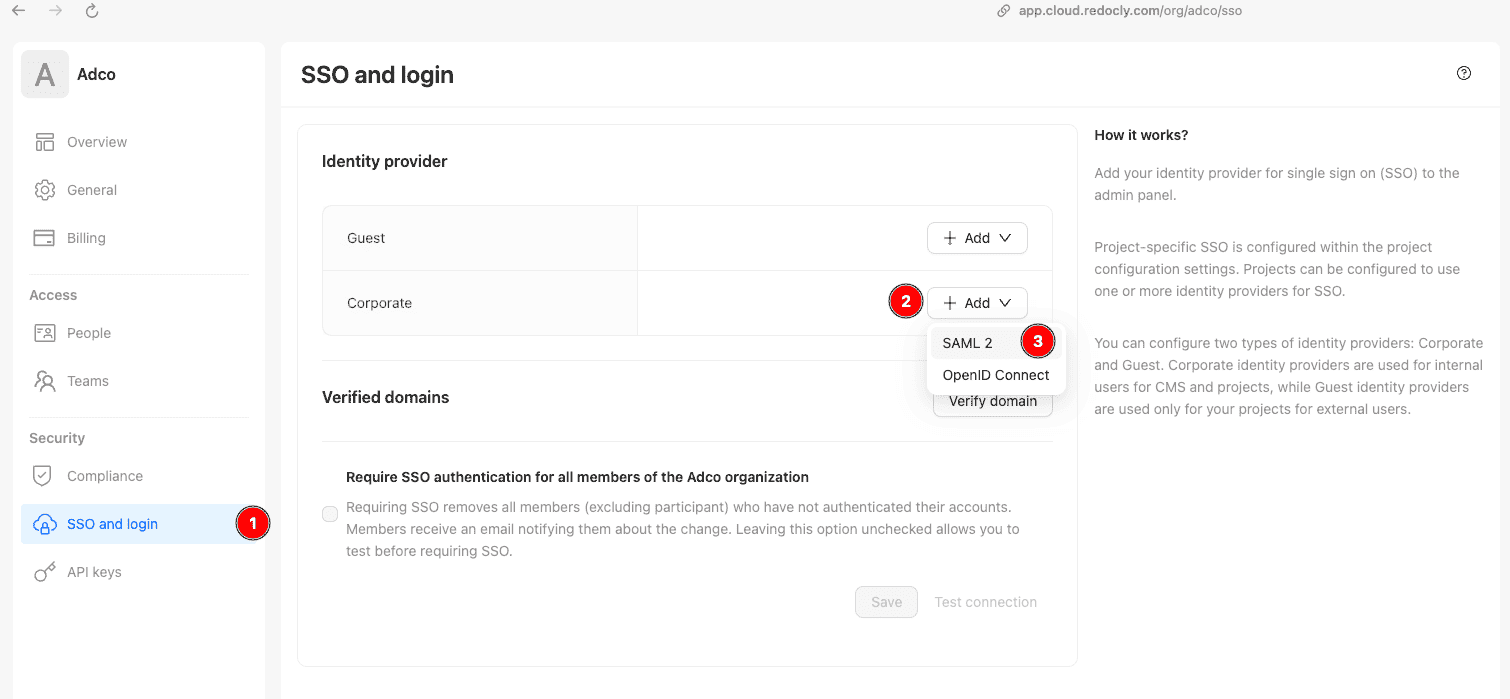
Keep this page open for reference, the values here are used in the next steps. After adding the required configuration in Microsoft Entra, return to this page to complete the final setup.
Install the Redocly Enterprise application from the Microsoft Entra gallery.
Assign some users and/or groups to the application:
- Go to the newly created Redocly application in and select Users and groups in the navigation.
- Select Add user/group.
- Select the users or groups that should have access to the Redocly application.
- Select the Default Access role
- Select Assign to grant their access.
Add the information needed for Microsoft Entra to connect to Redocly.
- Go to the application and select Single sign-on in the navigation.
- Select Edit on the Basic SAML Configuration card.
- Use the following values as appropriate for your region:
- Identifier (Entity ID):
<COPY VALUE FROM REDOCLY SAML SETUP PAGE> - Reply URL (ACS URL): https://auth.cloud.redocly.com/sso/saml/callback
- Sign on URL:
https://auth.cloud.redocly.com/org/<organization-id>
You can copy your organization ID from the URL: https://app.cloud.redocly.com/org/<organization-id>/`
Once you have entered the values for your region, select Save and then close the drawer.
Get ready to use group information from Microsoft Entra with Redocly RBAC by configuring the group claim.
- Go to the application in the Microsoft Entra and select Single sign-on in the navigation.
- Select Edit on the Attributes & Claims card.
- Select Add a group claim.
- Select the type of groups to use.
- Select Group ID as the attribute.
- Select Customize the name of the group claim and use
https://redocly.com/sso/teamsas the Name, as illustrated in the following screenshot.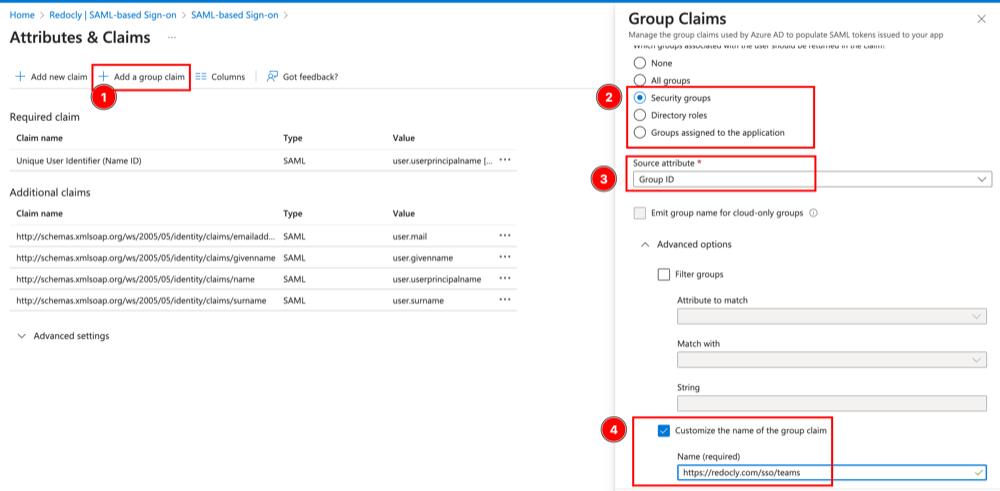
Go back to the Redocly SSO configuration screen that was opened earlier, and fill in the values from Microsoft Entra:
- Single sign on URL: Use the
Login URLfrom the Microsoft Entra Single sign-on screen. - Issuer ID: Use
Microsoft Entra Identifierfrom the SAML SSO setup screen. - X509 Certificate: Download the Base64 Certificate from the Microsoft Entra Single sign-on screen and paste the contents into this field.
Microsoft Entra doesn't send group names in the SAML response, so you may need to configure the team claim mapping in order to use human-readable team names for RBAC.
To do this, you need to Select Configure team claim mapping checkbox and add the mapping from the group ID to the team name.
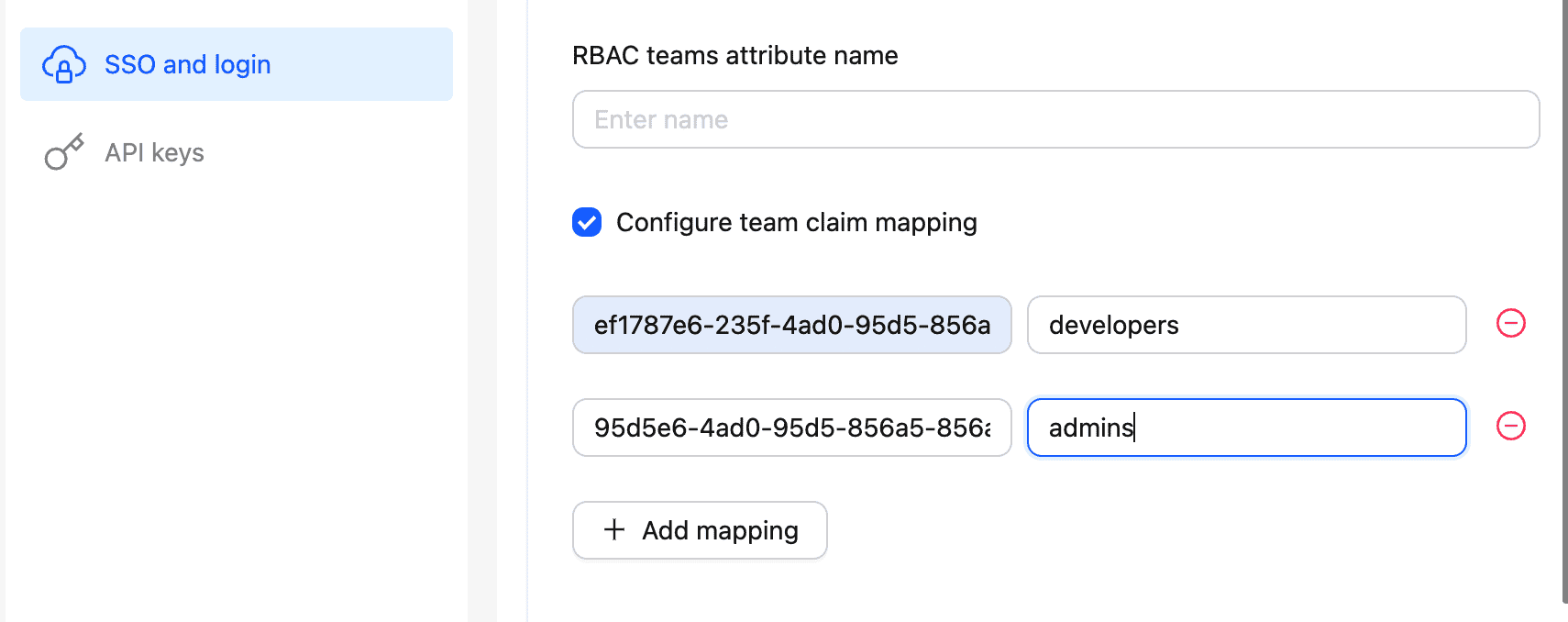
Select Save to finish the configuration.
To enable SSO login into Redocly Reunite, first verify the domain in the Redocly Reunite settings.
- Go to the Redocly Reunite dashboard and select SSO and login in the navigation.
- Select Verify domain.
- Enter the domain you want to verify and select Save.
- Let our support team know that you have requested domain verification.
To enable SSO for a specific project, add the sso section to the redocly.yaml file in the project repository.
sso:
- CORPORATE # or GUESTThis change must be committed to the main branch to take effect.
See the sso reference for more details.
You can configure RBAC using team names from Microsoft Entra.
Example configuration:
rbac:
content:
'**':
authenticated: read
apis/Team A/**:
authenticated: read
TeamA_member: maintain
TeamA_owner: admin
apis/Team B/**:
authenticated: read
TeamB_member: maintain
Team_B_owner: admin- SSO configuration reference - Complete technical reference for all SSO configuration options and settings in your redocly.yaml file
- RBAC configuration reference - Configure role-based access control options to manage user permissions and access levels